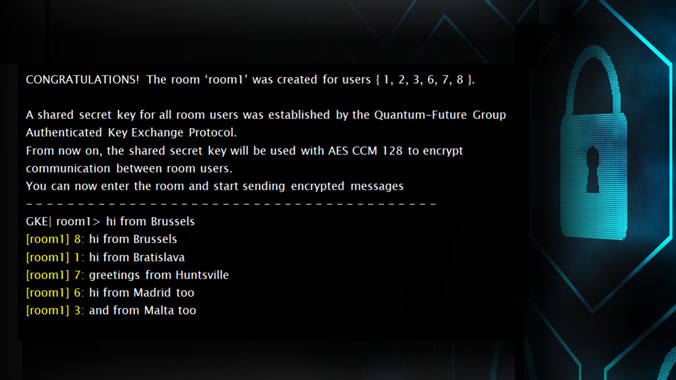
Bluefin: Don't forget about AES-256 in the fight against quantum threats - Inside Quantum Technology
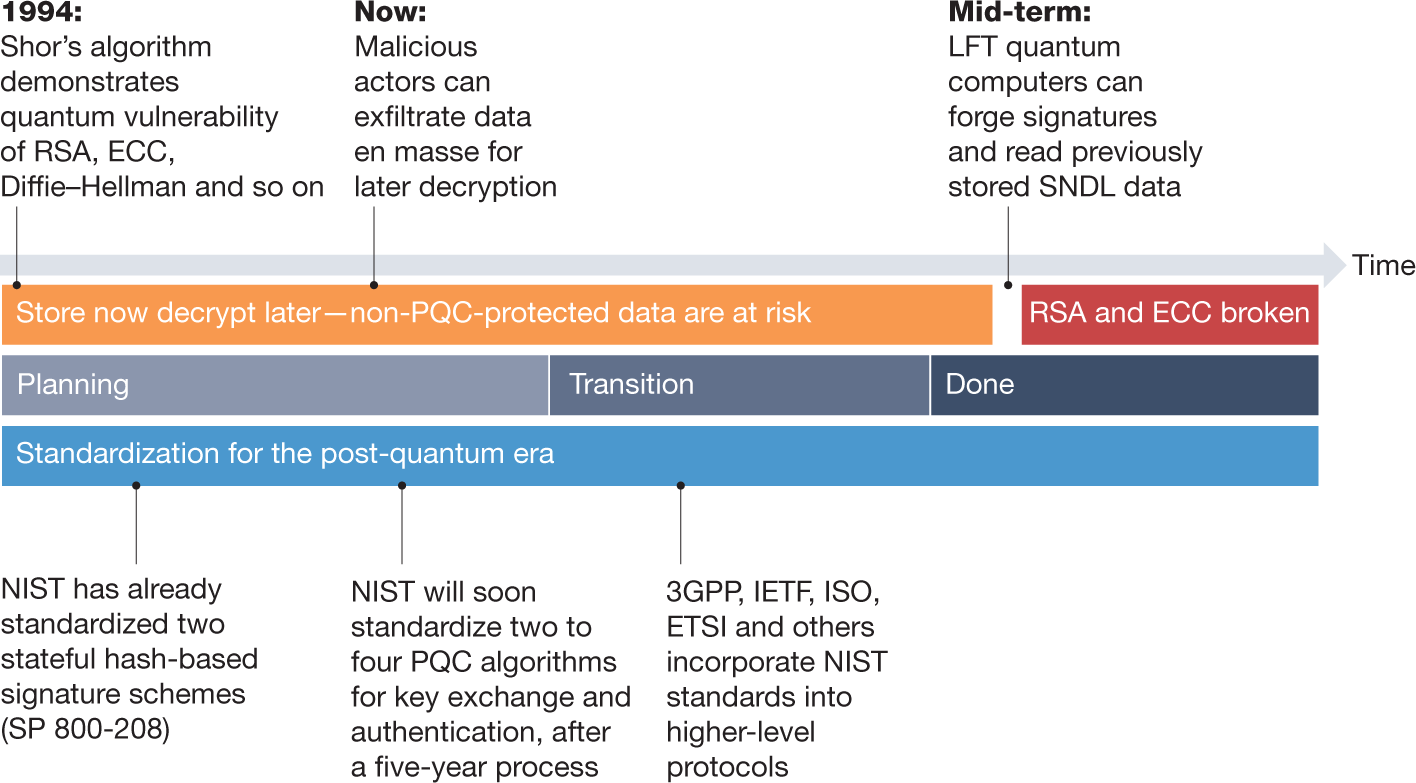
Quantum Safe Cryptography and Security - An introduction, benefits, enablers and challenges - June 2015

Will Symmetric and Asymmetric Encryption Withstand the Might of Quantum Computing? | Spiceworks It Security




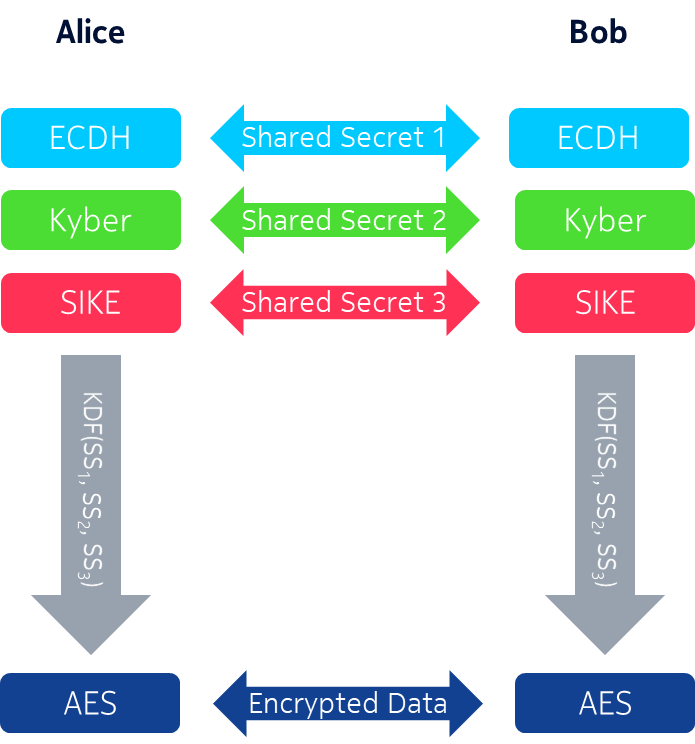



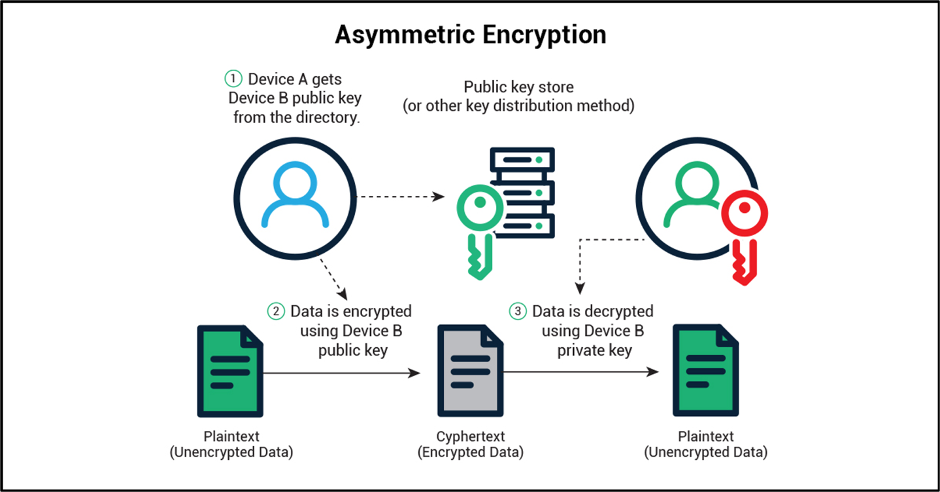
![What Is AES Encryption? [The Definitive Q&A Guide] What Is AES Encryption? [The Definitive Q&A Guide]](https://www.trentonsystems.com/hs-fs/hubfs/White%20and%20Yellow%20Simple%20Technology%20Keynote%20Video%20Presentation%20(6).png?width=690&name=White%20and%20Yellow%20Simple%20Technology%20Keynote%20Video%20Presentation%20(6).png)

![PDF] Surviving the Quantum Cryptocalypse | Semantic Scholar PDF] Surviving the Quantum Cryptocalypse | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/fb464da8aa1f54e92ddafe5ef693afb3f817b15f/4-Table1-1.png)